Sentry SSO with ServiceNow
Contents
- 1 Introduction
- 2 Setup AuthControl Sentry Keys
- 3 Setup SSO on ServiceNow
- 4 Configure Check Password with Repository on the Swivel Core
- 5 Setup AuthControl Sentry Application definition
- 6 Setup AuthControl Sentry Authentication definition
- 7 Testing connection with ServiceNow tool
- 8 Testing authentication to ServiceNow via Swivel AuthControl Sentry
- 9 Troubleshooting
Introduction
This document describes how to configure ServiceNow to work with Sentry SSO. Before following these instructions, you should be familiar with using Sentry - see the Sentry User Guide for more information.
Setup AuthControl Sentry Keys
Before you are able to create a Single Sign On configuration on yourdomain.service-now.com, you will need to setup some Keys if they were not set up already. Please see a separate article: HowToCreateKeysOnCmi. You will need the certificate you generate in a later section of this article. This can be retrieved from the View Keys menu option of Swivel AuthControl Sentry.
Setup SSO on ServiceNow
To configure SSO setting on your ServiceNow accounts you have to access your Admin console by simply going to https://yourdomain.servicenow.com You should see an Admin console.
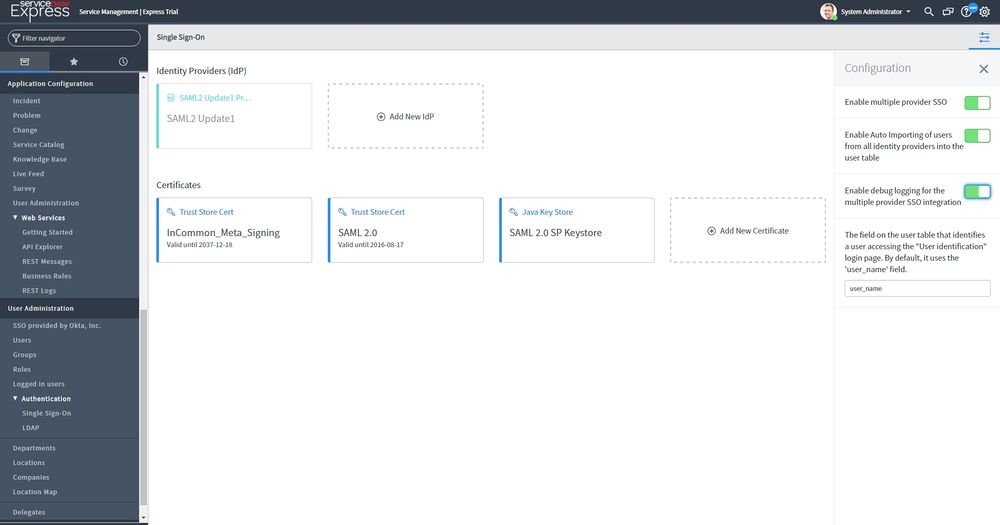
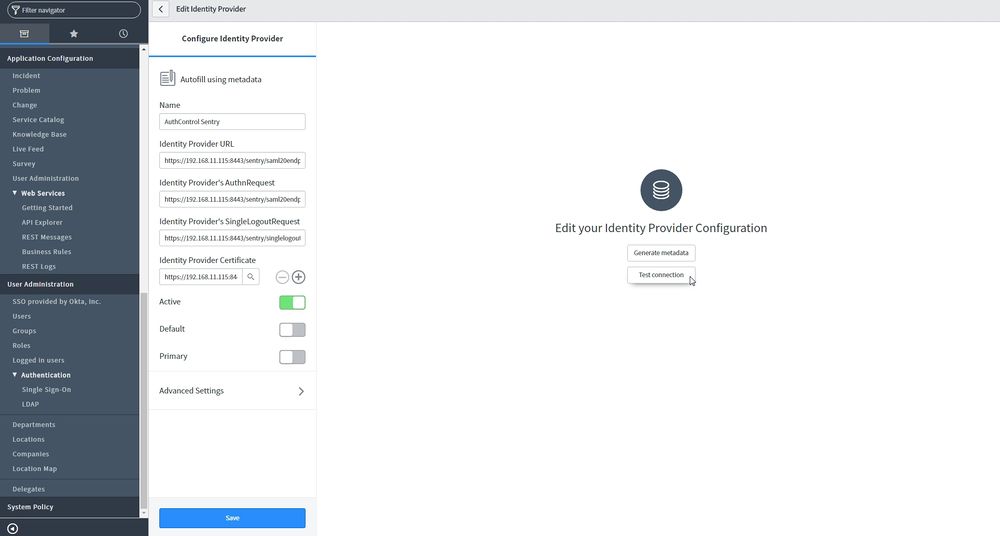
On the left menu you will see a User Administration section. When you click on the Single Sign-On you will be see the following screen. You have to enable the options displayed on the right, which are: "Enable multiple provider SSO" and "Enable Auto Importing of users from all identity providers into the user table" . Click on the button "Add New IdP" and select the User group for which to use SSO. For this example we are using "Swivel Users".
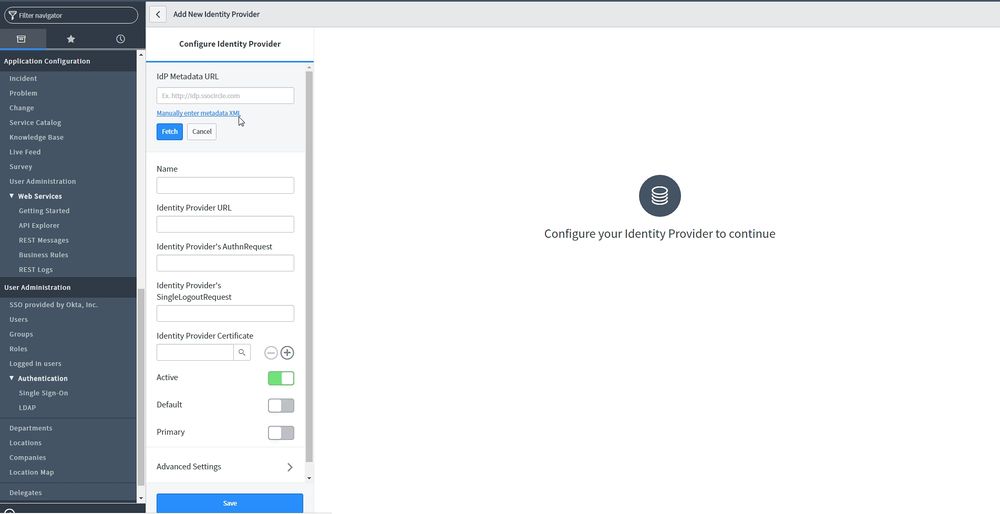
Click on the button "Add New IdP" and click "Manually enter metadata XML".
Now navigate to your AuthControl Sentry metadata page as below(https://<FQDN_OF_SENTRY_SERVER>/sentry/metadata/generatedMetadata.xml) and copy the content of this page.
Return back on the ServiceNow setup
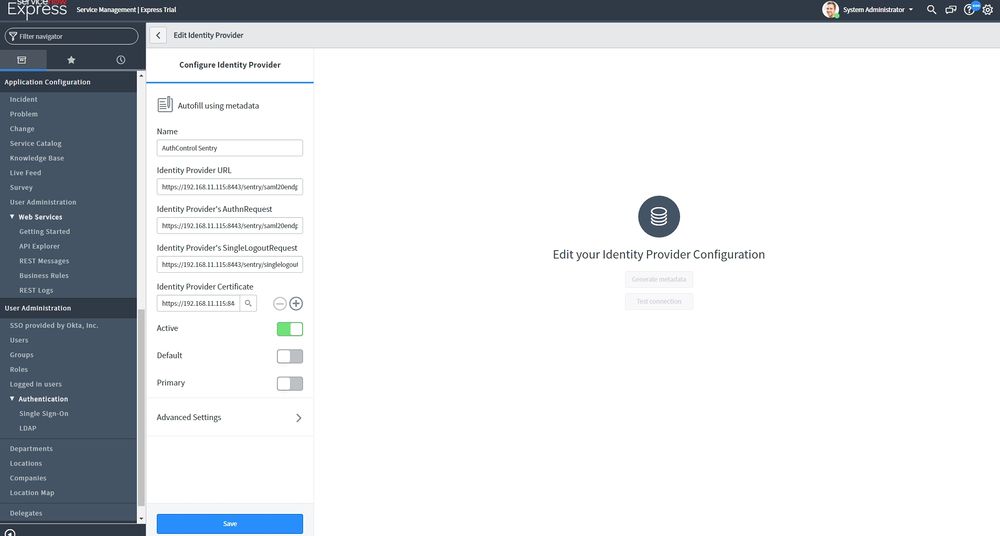
IdP Metadata XML - Paste copied metadata from your AuthControl Sentry and click Fetch. After that the following fields will be set automatically
Identity Provider URL
Identity Provider's SingleLogoutRequest
Identity Provider Certificate
You will have to fill the following ones for your AuthControl Sentry such as:
Identity Provider's AuthnRequest - Copy and paste the value set on "Identity Provider URL"
Active - Enabled
Default - Enabled
Primary - Enabled
After you have entered all the details as above click Save. You can test the connection after setting up Auth Control Sentry
Configure Check Password with Repository on the Swivel Core
In order to check the user’s Active Directory password, ensure that the local Agent defined under Server -> Agents has got the Check Password with repository checkbox enabled. When an authentication occurs in AuthControl Sentry, the Active Directory password will then be passed to Active Directory for verification.
Setup AuthControl Sentry Application definition
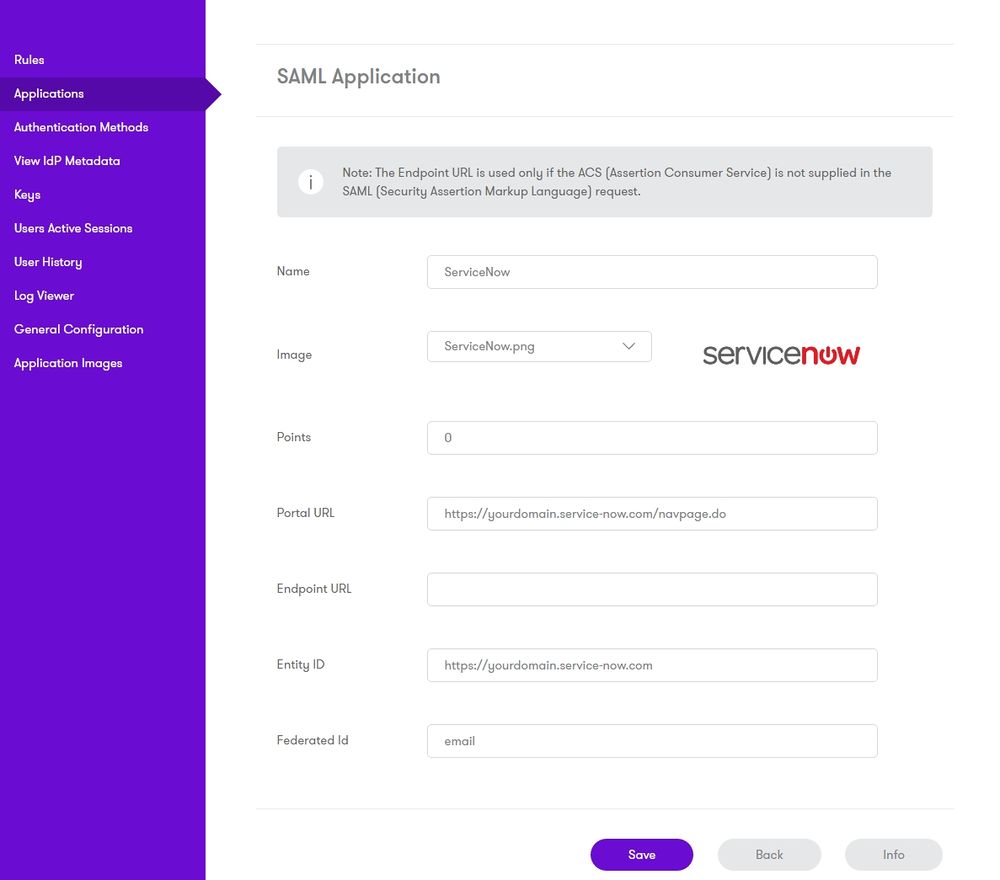
Login to the AuthControl Sentry Administration Console. Click Applications in the left hand menu. To add a new Application definition for ServiceNow, click the Add Provider button and select ServiceNow SAML.
Name: ServiceNow(Type an Arbitrary name for this Application)
Image: ServiceNow.jpg(selected by default)
Points: 100 (the number of points the user needs to score from their Authentication Method in order to successfully authenticate to this Application)
Portal URL: (this Portal URL is ServiceNow login URL which you can usually access on: https://yourdomain.service-now.com/navpage.do
Endpoint URL: N/A
Entity ID: https://yourdomain.service-now.com (Entity ID is the one defined on ServiceNow > User Administration > Single Sign-On > AuthControl Sentry Idp > Advanced Settings: Entity ID )
Federated Id: email
Setup AuthControl Sentry Authentication definition
As an example here we will be using Turing authentication as the Primary method required for ServiceNow authentication.
Login to the AuthControl Sentry Administration Console. Click Authentication Methods in the left hand menu. Click the Edit button against the Turing option in the list of Authentication Methods. Give this Authentication Method 100 points. This will mean that when a login attempt is made to the ServieNow Application, this Authentication Method will be offered during login. (Please read about AuthControl Sentry Rules and familiarize your self with AuthControl Sentry here )
Testing connection with ServiceNow tool
ServiceNow provides a tool to test the connection. Go to User Administration > Single Sign-On and click AuthControl Sentry Idp. After that click Test connection.
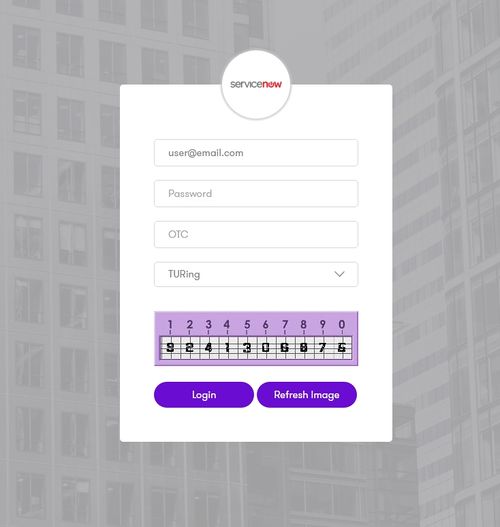
A new window will be displayed that will redirect to AuthControl sentry username page.
Once you have submitted your username. You should be presented with the page of the Authentication Method which can score enough points to match the points required by the ServiceNow Application definition.
In this login example we are using the email as a username
After we enter our authentication credentials we will see a logout screen. Close that window and on the ServiceNow page click View Log. Check that the logs indicate that the SAML authentication was successful.
Testing authentication to ServiceNow via Swivel AuthControl Sentry
This should be the final step after all previous elements have been configured.
In a web browser, visit the the URL that you setup on AuthControl Sentry as Endpoint URL e.g. https://yourdomain.service-now.com/navpage.do
Alternatively you can visit your AuthControl Sentry Page with your public DNS entry of your Swivel AuthControl Sentry server, e.g. https://mycompanysentrydomain/sentry/startPage On a Start Page you will be able to see a new ServiceNow Icon on which you can click and proceed with authentication (as you would by going straight to the ServiceNow page)
When you visit this URL you will notice that the domain should redirect to the identity provider login URL that you setup.
Once you have submitted your username. You should be presented with the page of the Authentication Method which can score enough points to match the points required by the ServiceNow Application definition.
In this login example we are using the email as a username
After we enter our authentication credentials we successfully will see the ServiceNow account that we tried to access.
Troubleshooting
There are various logging components available for this particular integration which can aid in diagnosis at different points during authentication.
- The Swivel Core has a Log Viewer menu item which can reveal information concerning user status e.g. is the user locked, has a session been started for the image request;
- The Swivel AuthControl Sentry has a View Log menu item which provides details about the SAML assertion and response received from ServiceNow
- The ServiceNow has a Test Connection feature that provides details about the SAML response received from AuthControl Sentry
It is crucial when troubleshooting, to pinpoint where the authentication is failing. For example, you may find that the Swivel Core logs show a successful authentication (which would indicate that the user has entered their Password and OTC correctly), but the AuthControl Sentry logging shows that there is a problem with the SAML assertion.
If you have issues login in with then SAML authentication to the admin console you can always access by https://yourdomain.service-now.com/side_door.do
Two common issues which can be diagnosed with the validator are:
- Certificate or decryption issues;
- Can AuthControl Sentry find the Certificate locally, is it the correct one?
- Has the correct Metadata been uploaded to the ServiceNow?
- Does the Repository -> Attribute name being used actually map to a Repository attribute? Has a User Sync occurred in the Swivel Core since modifying this?