Difference between revisions of "How To Configure OATH Mobile"
(→Overview) |
(→Configuring OATH policy settings) |
||
| Line 24: | Line 24: | ||
== Configuring OATH policy settings == | == Configuring OATH policy settings == | ||
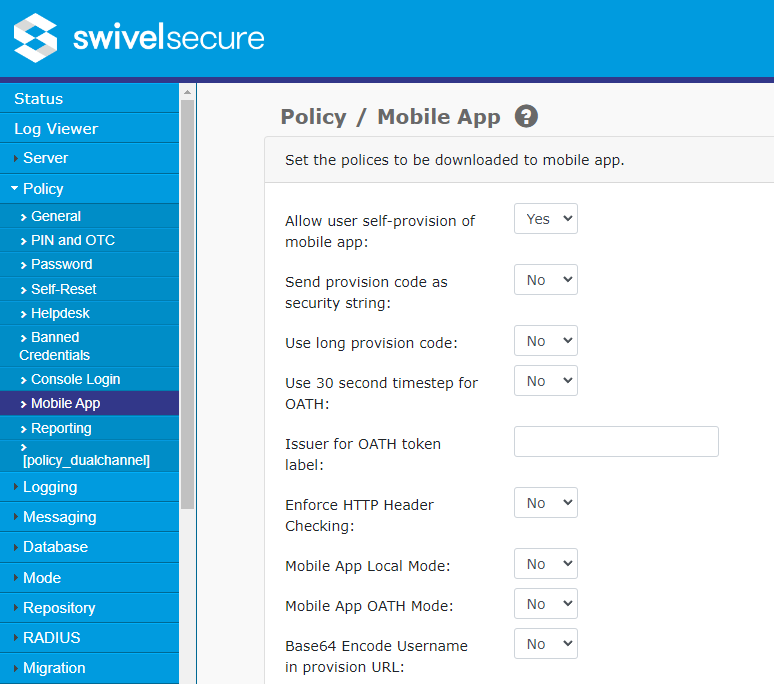
| − | On the Swivel Administration console select Policy | + | On the Swivel Administration console select Policy -> Mobile App and ensure the below settings are configured: |
Set '''Mobile App OATH Mode''' to Yes | Set '''Mobile App OATH Mode''' to Yes | ||
| − | + | [[File:PolicyMobileApp.png]] | |
| − | + | Other relevant options on this page are: | |
| + | |||
| + | * Use 30 second timestep for OATH - if this is enabled, OATH codes are compatible with Google and Microsoft Authenticators. AuthControl Mobile Authenticator also supports this. | ||
| + | * Issuer for OATH token label - this only applies to 30-second OATH mode, and sets part of the label for authenticator display | ||
== Define a group of Mobile OATH users == | == Define a group of Mobile OATH users == | ||
Revision as of 08:37, 28 September 2022
Contents
Overview
OATH authentication allows a mobile device to be prompted a new OTC every 60 seconds without requiring the connection to AuthControl Sentry. Optionally, this can be changed to every 30 seconds for compatibility with Google and Microsoft Authenticators. See below for more details.
Prerequisites
Swivel AuthControl Sentry v4 onwards
Swivel Mobile Phone Client Version v4 for One Touch Mobile client based solution.
Swivel Server Details SSD for mobile client with OATH enabled.
Swivel core configuration
In order for a user to be able to use the mobile app as a OATH token they must be allocated the right to use the OATH mode of operation. This is done by ensuring that they are a member of a group that has this right.
Mobile client users must install the Swivel Mobile Phone Client from the app store.
Configuring OATH policy settings
On the Swivel Administration console select Policy -> Mobile App and ensure the below settings are configured:
Set Mobile App OATH Mode to Yes
Other relevant options on this page are:
- Use 30 second timestep for OATH - if this is enabled, OATH codes are compatible with Google and Microsoft Authenticators. AuthControl Mobile Authenticator also supports this.
- Issuer for OATH token label - this only applies to 30-second OATH mode, and sets part of the label for authenticator display
Define a group of Mobile OATH users
On the Swivel Administration console, select a group of users that will be using Mobile OATH authentication and ensure that the OATH box is ticked then click Apply.
OATH Mobile Users
Testing
For testing OATH you can click App provision button on the user admin screen for the user that has been configured as a mobile OATH user and then provision the device with the URL or QR Code as explained:
Provision the device via URL. Please read more on Provision URL page.
Provision the device via QR code. Please read more on QR Code page.
Troubleshooting
Security code is showing instead of OATH Token
Please ensure that the SSD server for that Site ID has been configured as OATH and local mode is set to false. After changing the setting in SSD server, the users must me re-provisioned.
Check the Swivel logs for error messages
Error Messages:
CANNOT_CREATE_TOKEN for the <username> user does not belong to the OATH Group
This error can be seen where the button App Provision is clicked on the User Admin Console and the user does not have OATH permission. To solve that you need to add the OATH right to the group the user is member of.
OATH token does not allow the authentication.
When you click Provision App ensure that a token for that user has been created. For that you can go to the OATH/OATH Tokens screen and check that a new token has been created for that user.
If the token has not been created, ensure that the policy Mobile App OATH Mode is set to Yes.